A TLS Connector allows you to have a secure TCP socket without having any encryption or SDK's on the device.
What is TLS Connector?
A TLS Connector adds a layer of security to a normal TCP socket. First the device establishes a normal TCP connection, then Onomondo connects to a TLS server on your end which establishes a secure TLS socket, and finally pipes data between them both.
From the device's side it will look like a normal TCP socket, but from the server's side it will look like a secure TLS socket.
Quick note: A TLS Connector establishes an encrypted connection between device and server. Other Connectors communicate one-way sending events to the server (i.e. Microsoft Azure)
Example with HTTP
For simplicity we will use HTTP as it is a common example. So, HTTP and HTTPS are the same in the way they send data in every way, except HTTPS establishes a TLS (encrypted) connection before sending the information. So basically the TLS Connector is the adding the "S" into HTTPS. Here is a very basic overview.
- Updating the server to accept the dummy IP
- Stopping the server from checking the HOST header
- Adding the correct HOST header on the device
What needs to be set up?
- From the device side, you just need to use HTTP protocol and send the data to an HTTP endpoint.
- You need to set up an HTTPS server (for example on AWS/Heroku) to receive the information and include encryption key and crt files.
- On our platform create a Connector with the HTTPS endpoint and port number.

- Send HTTP request from the device
What is happening?
What will happen is when the data is received by the Connector, it will establish a TLS connection with the HTTPS endpoint and send the data securely to the endpoint.
As the HTTPS server has the encryption files, these will be exchanged while the TLS connection is being established. Key, Cert and CA parameters are optional and can be used to create stronger security.
Adding a Passthrough
An optional addition is setting up a passthrough. This identifies exceptions that the Connector will not pick and send to the HTTPS endpoint specified in the Connector. A couple of examples could be:
- Sending a ping - selecting the passthrough for packets with the ICMP protocol
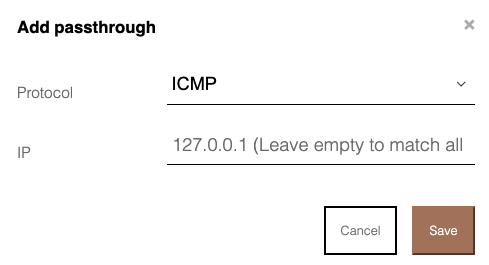
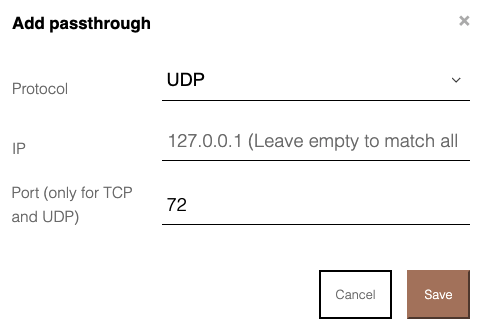
- Allowing DNS server lookup - selecting the passthrough for packets with the UDP protocol on port 53
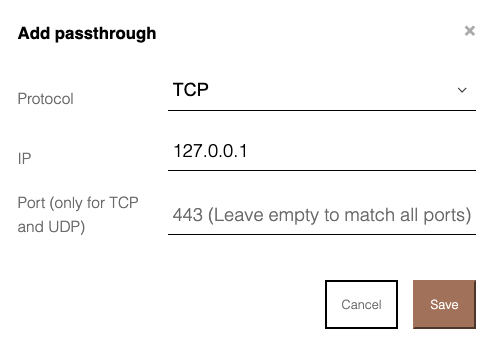
- Adding a FTP/Firmware update server - selecting a passthrough can also be set by a protocol and a specific IP address.
- Does TLS Connector only work with HTTP(S)?
No. It can be used whenever you have a TCP socket and need to establish a secure TLS connection, so that the device can talk with the server, for example could include a device sending a JSON object to a TLS server through a TLS Connector.
Not receiving the information at the endpoint?
One of the errors logged in the error log terminal is errors received between the server and the Connector. For more information, you can read the help article: What are error-logs?